
In a sensational case that has captured headlines, a Chinese engineer and two Filipino nationals were arrested for allegedly engaging in espionage activities against the Philippine government. Authorities claim the suspects were using advanced equipment for sensitive data collection, including 3D mapping. This incident raises serious questions about the Philippines’ national security and its capacity to handle cases involving sophisticated technology. However, the evidence presented—at least so far—appears inconclusive and invites further scrutiny.
The allegations hinge on the technical capabilities of the seized equipment and its alleged use in gathering data. Independent analyses and expert opinions have cast doubt on these claims, suggesting the setup may not be as advanced as portrayed. Moreover, the timing and coverage of this case have raised suspicions that it might be a political diversion. Is this truly a case of espionage, or an overreaction fueled by sensationalism? This article unpacks the technical, political, and strategic angles of this controversial incident.
Source:
Table of Contents
Are the Sequestered Equipment Truly Capable of Espionage?

A closer look at the equipment involved in the Chinese Engineer Arrest reveals potential discrepancies in its alleged purpose. Photos shared by the media show components such as a 4G modem, a TP-Link 5-Port PoE switch, a solar inverter, and a Nuvo-8000 series industrial computer. According to independent experts, these devices do not include SDR components, which are critical for intercepting cellular signals or spoofing SMS—common espionage tools.
While a DIY LiDAR or camera system was identified among the equipment, its capacity for 3D mapping falls short of the advanced tools typically used in state-sponsored operations. The hardware’s actual configuration suggests legitimate applications, such as mapping or logistics, rather than covert surveillance. Without stronger evidence, the claims in the Chinese Engineer Arrest lack substantial support.
Redundancy of 3D Mapping Tools in Modern Espionage
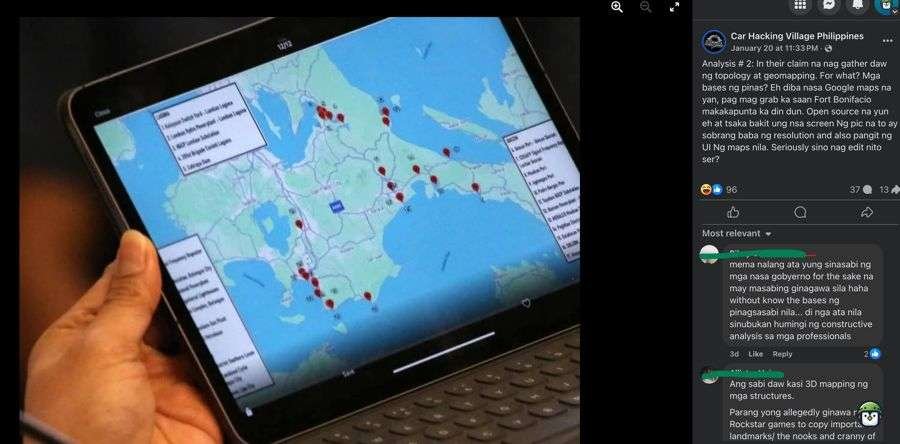
The claim that the suspects were conducting 3D mapping to gather sensitive geographic data seems redundant in today’s digital age. Platforms like Google Earth and OpenStreetMap provide high-resolution maps and satellite imagery for free. If China—a global leader in satellite technology—intended to conduct covert surveillance, it is far more plausible that they would use advanced satellite imaging rather than ground-based equipment that could be easily detected and intercepted. The narrative of espionage using 3D mapping tools appears less credible when considering the technological capabilities available to state actors.
Questions of Verification and Credibility
The narrative of espionage through 3D mapping, as alleged in the arrest, appears redundant in an era where platforms like Google Earth and OpenStreetMap provide high-resolution imagery for free. If a state actor like China intended to gather sensitive geographic data, advanced satellite imaging would offer a far more covert and effective method. This casts further doubt on the plausibility of the allegations tied to the hacking incident.
A Potential Diversionary Tactic
This case has drawn significant public attention, conveniently diverting focus from more pressing issues such as inflation, unemployment, and the ongoing maritime disputes in the West Philippine Sea. The sensational nature of the allegations may serve political interests, whether by the administration or the opposition. By framing this incident as a grave national security threat, political actors could be leveraging public concern to shift the narrative and deflect accountability.
Independent Analysis of the Equipment
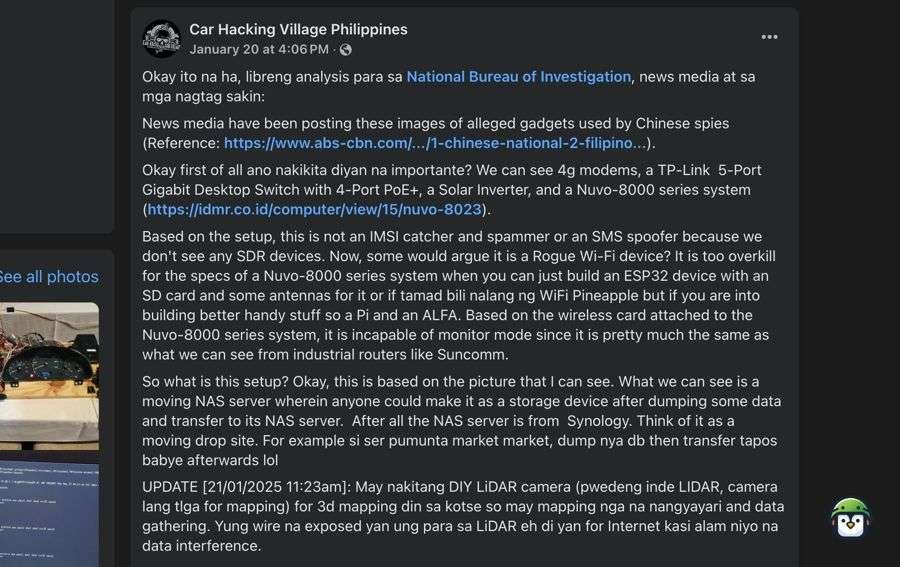
The Car Hacking Facebook Group conducted an independent analysis of the seized devices, shedding light on their actual capabilities. The findings reveal:
- The equipment included a 4G modem, a TP-Link PoE switch, and a Nuvo-8000 system, suggesting it functioned as a mobile NAS server.
- The absence of SDR devices or other tools necessary for wireless interception debunks the theory of advanced espionage.
- A DIY LiDAR or camera system, likely used for basic 3D mapping, was identified but lacks the sophistication for state-sponsored operations.
- Exposed wiring and amateur assembly suggest a lack of technical precision, further casting doubt on the espionage narrative.
Art Samaniego Jr. highlights that while the equipment in question may seem outdated, its effectiveness depends on the user’s expertise and intent. Even low-powered devices, such as a Raspberry Pi, can achieve significant results when handled creatively and skillfully. The hardware’s potential is defined more by its application than its specifications.
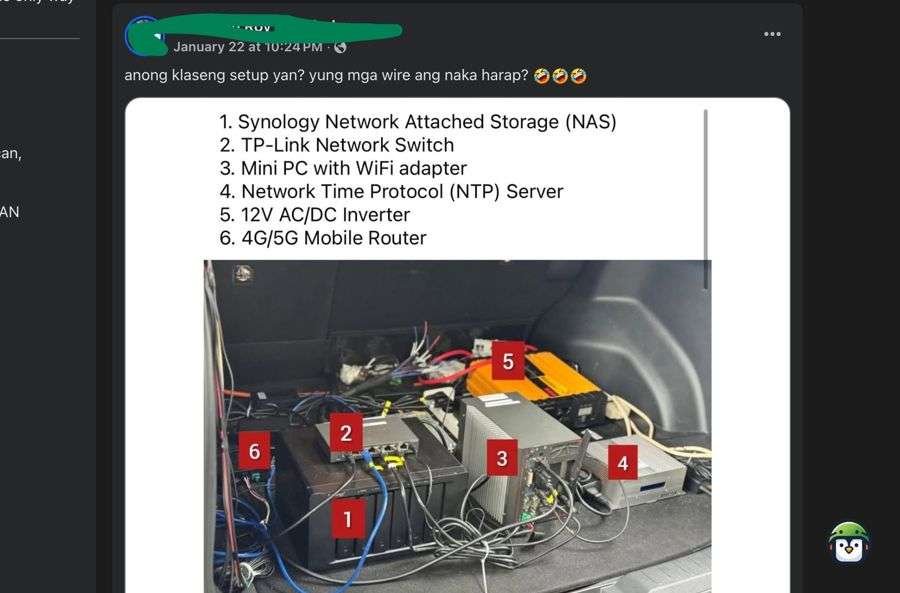
The setup described appears to function as a mobile network or computing station, suitable for communications, data processing, or monitoring tasks. Key components include:
- Power inverter to convert vehicle power for equipment use.
- Mini-PC/router with antenna for wireless communication (4G/5G, Wi-Fi, etc.).
- Storage device or card reader for secure data handling.
- Synology NAS or similar device for data storage.
- Network switch to connect multiple devices.
- Interconnecting cables for data and power transmission.
Potential uses for this setup range from establishing mobile communications or surveillance hubs to penetration testing and data interception, depending on the software and configuration. This highlights how even seemingly simple setups can be adapted for advanced applications.
Conclusion
The arrest of the Chinese engineer and two Filipinos has raised important questions about the Philippines’ security and its handling of alleged espionage cases. However, the evidence provided so far does not strongly support the government’s claims. The seized equipment lacks the sophistication typically associated with covert surveillance, and the narrative of espionage appears overstated without technical validation.
This incident also highlights broader concerns about political motivations and the potential for diversionary tactics. By focusing public attention on alleged espionage, the government may be diverting scrutiny from critical national issues. Transparency and accountability are essential to ensure that this case is investigated fairly and that the public is not misled for political gain. The real lesson here is the need for independent technical expertise to evaluate such incidents objectively, avoiding sensationalism and focusing on evidence-based conclusions.

Leave a Reply